BruteForcer download

As high-bit encryption keys are practically immune to current brute force attacks, it is recommended that all web services that collect user information encrypt their data and communications using 256-bit encryption keys. Therefore, you can also run it against encrypted password storage. He is currently a researcher with InfoSec Institute. This is the case, for example, in critical applications where any errors in the would have very serious consequences; or when. Although the limbs designate these weights, they do have a 20 pound weight range.
Brute Force Attack

His area of interest is web penetration testing. Further, no arrangement with two queens on the same row or the same column can be a solution. For 256-bit encryption, an attacker would have to try 2 256 different combinations, which would require 2 128 times more computational power to crack than a 128-bit key! Wait till you've played the game before you review it. It basically performs dictionary attacks against a wireless network to guess the password. This way they do not need to remember complex passwords and have multiple accounts.
brute force : German » English

Recent computers manufactured within the last 10ish years can brute force crack an 8 character alphanumeric password — capitals and lowercase letters, numbers, and special characters — in about two hours. Mit bequem verfügbaren Schlüsseln ist der Zugang zu den meisten Informationen in Echtzeit gewährleistet. Indeed, brute-force search can be viewed as the simplest. To protect your Magento backend against hackers and brute-force attacks , you may need to change the Magento backend root. In 2005 all chess game endings with six pieces or less were solved, showing the result of each position if played perfectly. It supports over 400 hashing algorithms. This tool is now open source and you can download the source code.
Brute force
People how often shoot in cold weather may appreciate this attribute. Echtzeit-Zugang zu verschlüsselten Daten Im Gegensatz zu früher genutzten Methoden, die auf langatmige Wörterbuch-Angriffe oder Brute Force-Passwortermittlung zurückgreifen, kann das neue Toolkit die meisten Schlüssel aus dem physischen Gerät extrahieren. This unwelcome phenomenon is commonly called the , or the. Dual cam bows are generally seen as more comfortable to shoot, and have a rock solid back wall. I agree to receive these communications from SourceForge.
Brute
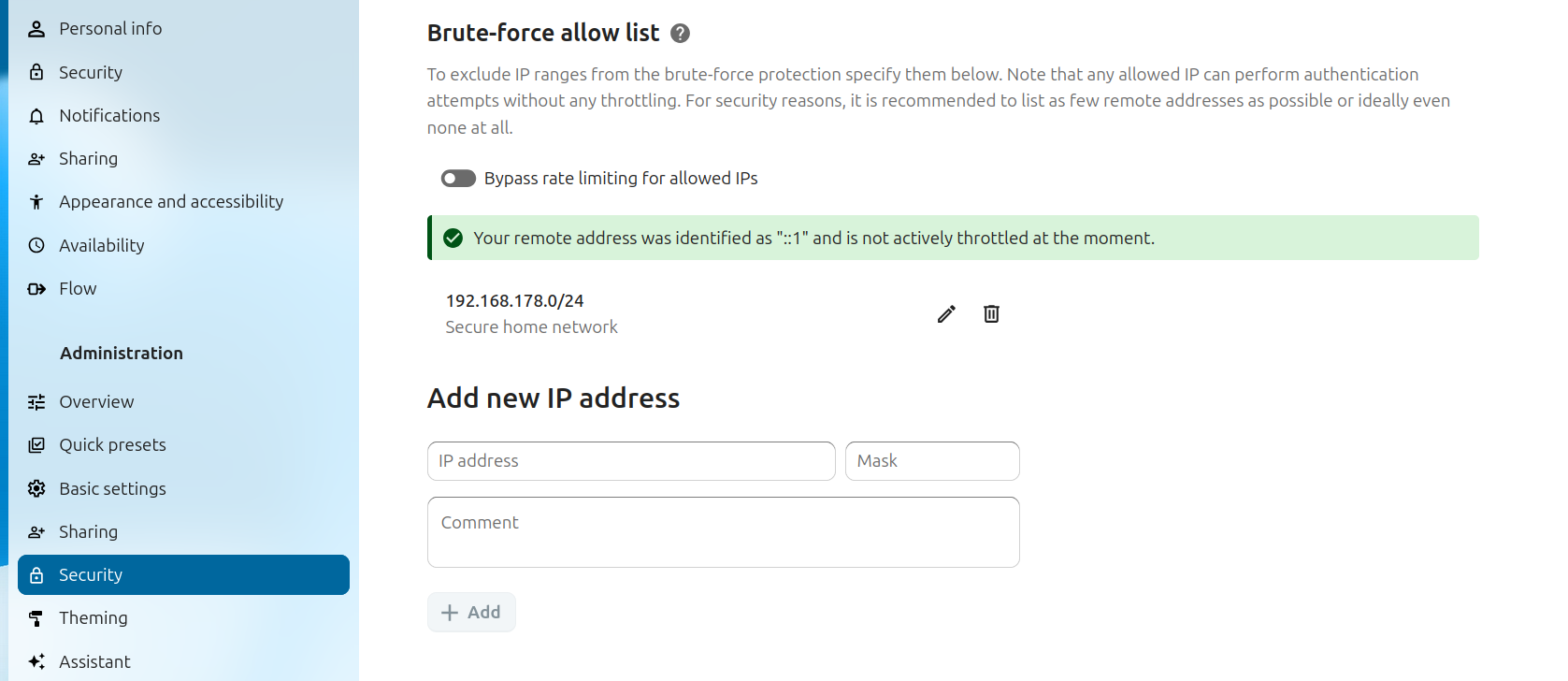
Um Ihren Magento-Backend gegen Hacker und Brute-Force-Angriffen zu schützen, verändern Sie den Root von Magento-Backend. It does not make brute-force impossible but it makes brute-force difficult. Brute-Force-Angriffe Brute-Force-Angriffe sind sehr gefährlich, da alle möglichen Schlüssel angewandt werden, um ein Verfahren anzugreifen. In this way, it is different from other conventional brute-forcing tools. We analyze your responses and can determine when you are ready to sit for the test. The best way to prevent brute-force attack is to limit invalid login.
Brute Force
Cam System The cams on this bow are one of its biggest selling points. You can try on given platforms to see how this tool works. The official page for the tool is dead but the tool can be downloaded from github. Tool dependency or use of scripts to generate custom lists. This makes it hard for attacker to guess the password, and brute-force attacks will take too much time.
brute force : German » English

To give you a sense of what these numbers mean, a powerful computer that could check trillions of combinations per second would still require well over a sexdecillion years to crack a 256-bit encryption key a sexdecillion is a one followed by 96 zeroes. It can perform different attacks including brute-forcing attacks. This will take more time but will be effective. Komplexe Passcodes können ermittelt werden, erfordern jedoch mehr Zeit. I also mentioned this tool in our older post on most popular password cracking tools.
brute translation German

The hacking community has developed various tools and techniques to perform brute force attacks. There is not generally a huge amount of maintenance these days, but will require more frequent inspection. Download John the Ripper from this link: Rainbow Crack Rainbow Crack is also a popular brute-forcing tool used for password cracking. For 20 letters, the number of candidates is 20! It protects the database against protocol attacks , brute-force password attacks , etc. Just like passwords, encryption keys can be cracked using brute force attacks, but today there are encryption keys in use that would take so long to crack using modern computers that they are considered as good as unbreakable. Other rainbow tables are also available to download.
What is a Brute Force Attack? Definition

It took ten more years to complete the tablebase with one more chess piece added, thus completing a 7-piece tablebase. It is fully customisable and has a scheduler as well for automated tasks. On the other, the physicists use a critical system to generate the password image. Despite some very well thought out ideas employed to control a group of characters and a mulitude of different weapons, the game has almost nothing in the way of a storyline, mission briefings are just intermissions between shoot outs, and weapon effects are painfully lacking; especially for a game on the most powerfull console on the market today. Don't play well with others? Play alone through six different worlds in the extensive single-player campaign, or grab up to three of your friends to jump in on-the-fly in dynamic cooperative mode. Determine which required skills your knowledge is sufficient 2.
Partner finden wien
Übergewicht schwanger werden
Geschenke für jahrestag beziehung
Комментариев нет:
Отправить комментарий